Implementation of a set of EC2 instances using Terraform and AWS Systems Manager configuration with Amazon Simple Notification Service for automated installation of security officers.

Project description:
In this project based on a real-world scenario, I acted as DevSecOps Engineer, and I deployed a set of EC2 instances and infrastructure in an automated way using Terraform (infrastructure as code — IaC). Also, it was necessary to install a specific security agent on all these instances in an automated way.
Once I provisioned the infrastructure, AWS System Manager and its component Command Run were used to install the security agents in an automated way. I used the Amazon Simple Notification Service — SNS to send an email informing the whole process status.

Project Overview :
This project will have (2) parts. The first part is to use Terraform to provision the (2) EC2 instances. These (2) instances will be web servers. The second part will be using the Run Command to pre-install these (2) web server with a security agent, which is a requirement, by default.
Part 1 : Terraform — Provision EC2 Instances
- I used Microsoft Visual Code to check the configuration files using Terraform. The file is confirmed to be ready for use after the VPC and subnet entries have been edited and verified.
- We must generate a security key in order to access both EC2 instances securely since we are configuring SS0H access to them. Use the SSH key_name that is specified in the configuration file.
Installing Terraform on the AWS Cloud Shell was the next task I had. The steps are as follows:




- Install Terraform on AWS Cloud Shell
sudo yum install -y yum-utils
sudo yum-config-manager — add-repo https://rpm.releases.hashicorp.com/AmazonLinux/hashicorp.repo
sudo yum -y install terraform





Terraform
Step 1 — terraform init
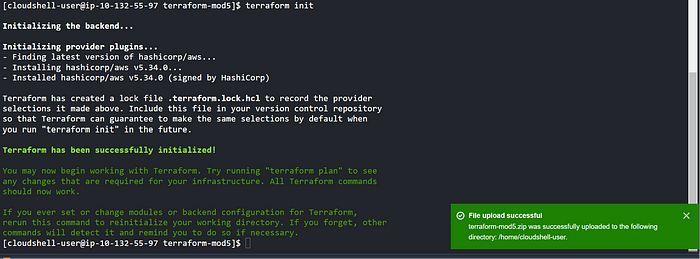
Step 2 — terraform plan
I face error problem log error
Solve this cmd
terraform init -migrate-state
TF_LOG=trace terraform init


Terraform Plan:







Step 2 — Create a new SNS topic
Go to SNS dashboard
Click topics, create new topic



copy
Topic ARN:
arn:aws:sns:us-east-1:434658200296:DevOpsNotification
Subscription ARN:
arn:aws:sns:us-east-1:434658200296:DevOpsNotification:a2192dce-243e-4f41-b93c-8fe5a005b70a


Step 4 — Configure the System Manager
Go to the AWS System Manager dashboard
Click quick setup (on left)
Click Create
Choose host management and click next

Change to manual selection for targets.
Click check box to install on all targets
Click create.


Click on “Session manager”
We want to click on Start Session but none of the EC2 instances are showing in the console — Troubleshoot LESSON!!!!!!
I found a AWS support article on at https://repost.aws/knowledge-center/systems-manager-ec2-instance-not-appear
After checking the items outlined in the article without any fixing the issue, the article suggests to check the logs on the server. The SSM Agent logs are in /var/log/amazon/ssm
The logs suggested the EC2 instances may need to be rebooted in order to appear here for connecting. After rebooting both EC2 instances, the issue is fixed and they both appear as “Target Instances”



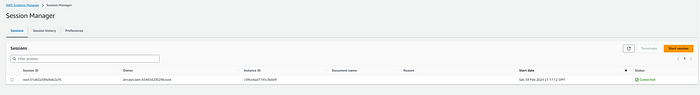
- Execute “Run Command” to deploy the “security agent instalation”
— Command document: AWS-RunShellScript
— Command parameters:
sudo wget -q https://tcb-bootcamps.s3.amazonaws.com/bootcamp-aws/en/install_security_agent.sh -P /tmp
sudo chmod +x /tmp/install_security_agent.sh
sudo /tmp/install_security_agent.sh
ls -ltr /usr/bin/security_agent




Here is the email notification that I received.
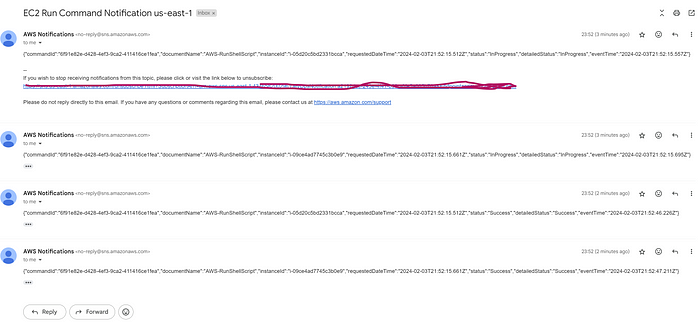


security_agent check,
ls -ltr /usr/bin/security_agent



Removing resources:

sudo yum install -y yum-utils
sudo yum-config-manager — add-repo https://rpm.releases.hashicorp.com/AmazonLinux/hashicorp.repo
sudo yum -y install terraform
ls [terraform state file]
terraform destroy


Instead of using the console for this project, we used Terraform to provision two EC2 instances and create a security group. Additionally, we installed a security agent on the two web servers using the Run Command in the AWS System Manager. Additionally, we configured AWS System Manager to send status updates on these installations via the Amazon Simple Notification Service.
